A new and major ransomware attack is currently spreading throughout Europe. Although there have only been a small number of reported cases in the US, we wanted to be as proactive as possible and share this information with our valued clients, friends and colleagues. Please read the following information and share it with your family, friends, co-workers and end users.
A new and major ransomware attack is currently spreading throughout Europe. Although there have only been a small number of reported cases in the US, we wanted to be as proactive as possible and share this information with our valued clients, friends and colleagues. Please read the following information and share it with your family, friends, co-workers and end users.
How It Works & What to Look For
The Bad Rabbit ransomware functions in a similar way as the recent NotPetya/Petya attacks, encrypting your files first and then your file system; leaving you with a ransom lock screen that is displayed before Windows starts. Unlike other recent malware epidemics, which spread through more passive means, Bad Rabbit requires a potential victim to download and execute a bogus Adobe Flash installer file, thereby infecting themselves.
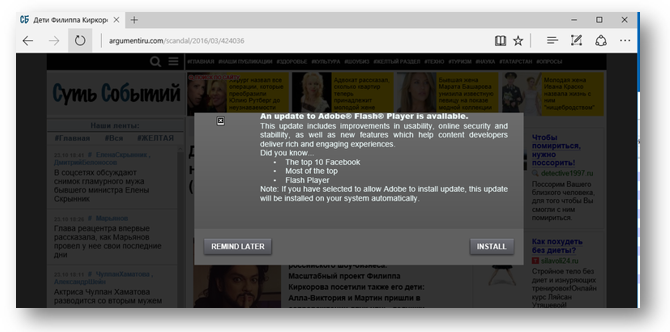
Essentially, Bad Rabbit spreads via hacked websites. When a user comes across one of these sites, the ransomware will ask the user to update their Adobe Flash and activating the attack -- See below:
Why It’s Dangerous
Unlike many of the major ransomwares in the recent past, Bad Rabbit has the ability to spread laterally across networks and then propagate without user interaction. This means once a machine is infected, it has the potential of infected everything it is connected too (i.e. servers, other computers within same infrastructure).
Users with computers infected with the malware are then asked to pay .05 Bitcoin or roughly $276 USD in exchange for their data in a set amount of time. A countdown on the site will show the amount of time before the ransom price goes up.
Help Ransomware - What You Should Do
If you are a LANTIUM client, call support immediately if you are prompted to install any software or updates that you are not sure about. If you are not a LANTIUM client, you should immediately call your organizitions primary IT department/support company/contact. If you do not have a reliable IT support provider, it may be time to consider one.
To Our Valued Clients - You're Safe!
Please be aware that LANTIUM is constantly monitoring and updating operating systems as a service to all of our managed services clients. We understand the seriousness of this and all other cyberattacks and the effect it can have on your business.
Although this ransomware attack has proven to be successful globally, we do not foresee any issues in the environments of our managed service clients due to our ongoing efforts to patch workstations and servers regularly.
How Do I Know if I Have Been Infected?
Sometimes even taking every precaution is not enough for IT security, which is why knowing what to look for and how to detect the symptoms of a compromised computer is important to ensure your safety. Read our recent post, 5 Symptoms of a Compromised Computer, to know if you have been infected and if your data and network is at risk.
How to Protect Your Business from Ransomware
Practicing good cyber hygiene is the best way to protect yourself, your workplace, and data from cyberattacks. A few technical considerations are listed below. All of them you may do on your own or contact LANTIUM for assistance:
- Enable strong spam filters, and scan all inbound and outbound emails with filters
- Configure firewalls to block access to known malicious IP addresses
- Patch all operating systems, software, firmware
- Set antivirus and antimalware programs to scan automatically
- Manage use of sensitive accounts on the principle of least privilege
- Consider disabling Remote Desktop Protocol
- Use application whitelisting and backup data regularly
- Conduct annual penetration testing
The truth is, there’s no excuse for leaving yourself or your business exposed. Please read our recent post, Seven Simple Habits to Protect Your Business from Ransomware, for things to do now for basic data breach prevention, minimize risk, and to keep you, your end users and business safe.
What to Do if You’re Infected
Panic and worry can be overwhelming once you realize that your computer may have been compromised. However, it’s not over for your computer and all of your files. If you believe you have been infected by a virus, trojan, worm, ransomware, or cryptolocker, there is still a chance to restore your computer to the state it was prior to infection, quickly, and without further damage or loss of productivity.
If you believe your computer may be infected, or if your organization has had IT security and performance issues in the past, Lantium can help! Our Critical Care support team is available for our clients 24x7x365.
Interested in learning more about security audits, proactive monitoring, data backup, or how to make your business and its data more secure? Schedule a free call with our experienced security consultants today: